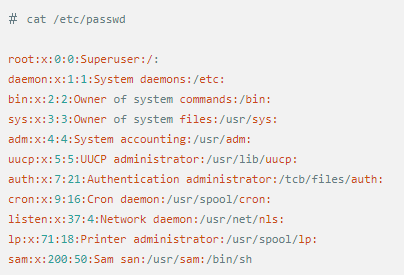
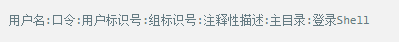
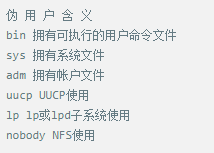
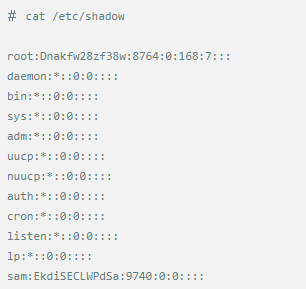
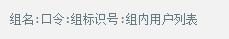
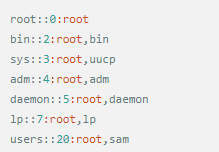
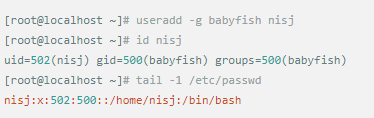
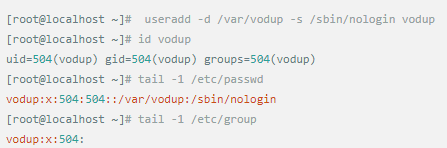
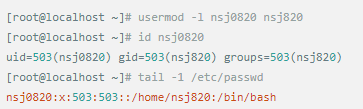
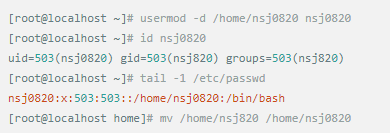
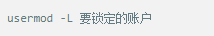
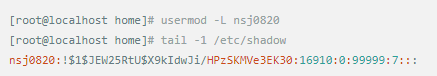
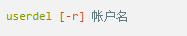
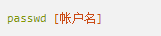
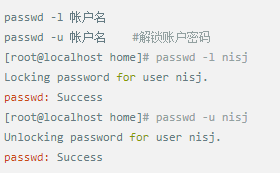
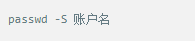
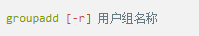
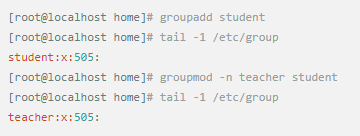
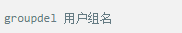
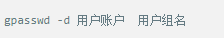
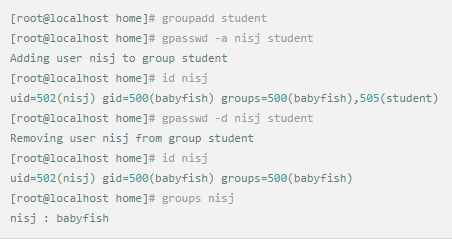
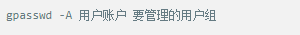
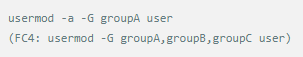
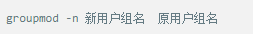Whether it's the nature of Linux's own multi-user multitasking and time-sharing operating system, or for system security reasons, Linux users and user groups are among the most important pieces of the system. Whether it is daily use, or as a server to apply Linux, creating the right users, groups, and giving the appropriate permissions is a basic use technique. Today Xiaobian compiled the contents of Linux user and user group management for everyone. The whole text is more than 10,000 words, trying to show the whole picture of Linux user management. If you are not familiar with this knowledge, then you must read the article carefully~ Overview The Linux system is a multi-user multi-tasking time-sharing operating system. Any user who wants to use system resources must first apply for an account to the system administrator and then enter the system as the account. On the one hand, the user's account can help system administrators to track the users who use the system and control their access to system resources. On the other hand, it can help users organize files and provide users with security protection. Each user account has a unique username and its own password. Once the user types the correct username and password when logging in, they are able to enter the system and their home directory. There are many ways to accomplish user-managed work, but each method actually modifies the relevant system files. User Management File Introduction Information about users and user groups is stored in system files, including /etc/passwd, /etc/shadow, /etc/group, and so on. The contents of these files are described separately below. 1. /etc/passwd The /etc/passwd file is the most important file involved in user management. Each user in the Linux system has a corresponding record line in the /etc/passwd file that records some of the basic properties of the user. This file is readable by all users. Its content is similar to the following example: From the above example, we can see that a row of records in /etc/passwd corresponds to a user, and each row of records is separated into 7 fields by a colon (:). The format and specific meaning are as follows: 1) "User Name" is a string representing a user account. Usually no more than 8 characters in length and consists of uppercase and lowercase letters and/or numbers. There can be no colon (:) in the login name, because the colon is a separator here. For compatibility reasons, it is best not to include dot characters (.) in the login name, and do not start with a hyphen (-) and a plus sign (+). 2) "Password" In some systems, the encrypted user password is stored. Although this field stores only the encrypted string of the user's password, it is not plain text, but since the /etc/passwd file is readable by all users, this is still a security risk. Therefore, many Linux systems (such as SVR4) now use shadow technology to store the actual encrypted user password in the /etc/shadow file, and only store a special one in the password field of the /etc/passwd file. Character, such as "x" or "*". 3) "User ID" is an integer that is used internally by the system to identify the user. In general, it has a one-to-one correspondence with the user name. If the user IDs corresponding to several user names are the same, they will be treated as the same user internally, but they can have different passwords, different home directories, and different login shells. The value of the user ID is in the range of 0 to 65 535. 0 is the ID of the super user root, and 1 to 99 is reserved by the system. As the management account, the ID of the common user starts from 100. In Linux systems, this limit is 500. 4) The "Group ID Number" field records the user group to which the user belongs. It corresponds to a record in the /etc/group file. 5) The "Annotative Description" field records some of the user's personal circumstances. For example, the user's real name, phone number, address, etc., this field has no practical use. The format of this field is not uniform on different Linux systems. In many Linux systems, this field holds an arbitrary annotative description text that is used as the output of the finger command. 6) "Home Directory", which is the user's starting working directory. It is the directory where users are logged in to the system. In most systems, each user's home directory is organized in the same specific directory, and the user's home directory name is the user's login name. Each user has read, write, and execute (search) permissions on their home directory, and other users' access rights to this directory are set according to specific conditions. 7) After the user logs in, a process is started to transfer the user's operation to the kernel. This process is a command interpreter or a specific program that is run after the user logs in to the system, that is, the shell. The shell is the interface between the user and the Linux system. There are many kinds of Linux shells, each with different characteristics. Commonly used are sh (Bourne Shell), csh (C Shell), ksh (Korn Shell), tcsh (TENEX/TOPS-20 type C Shell), bash (Bourne Again Shell) and the like. The system administrator can specify a shell for the user based on system conditions and user habits. If you do not specify a shell, the system uses sh as the default login shell, that is, the value of this field is /bin/sh. The user's login shell can also be specified as a specific program (this program is not a command interpreter). With this feature, we can restrict users to only run the specified application, and the user will automatically quit the system after the application finishes running. Some Linux systems require only those programs that are registered in the system to appear in this field. 8) One type of user in the system is called psuedo users. These users also have a record in the /etc/passwd file, but they cannot log in because their login shell is empty. Their existence is mainly to facilitate system management and meet the requirements of the corresponding system process for the file owner. Common pseudo-users are as follows: Other account files 1. In addition to the pseudo-users listed above, there are many standard pseudo-users, such as audit, cron, mail, usenet, etc., which are also required for related processes and files. Since the /etc/passwd file is readable by all users, if the user's password is too simple or the rules are obvious, an ordinary computer can easily crack it, so the Linux system with high security requirements is required. The encrypted passwords are separated and stored in a separate file. This file is the /etc/shadow file. A superuser has the file read permission, which ensures the security of the user's password. 2. The record line in /etc/shadow corresponds to one-to-one in /etc/passwd. It is automatically generated by the pwconv command based on the data in /etc/passwd. Its file format is similar to /etc/passwd and consists of several fields separated by ":". These fields are: "Login name" is the user account that matches the login name in the /etc/passwd file. The "Password" field stores the encrypted user password, which is 13 characters long. If it is empty, the corresponding user does not have a password, and does not need a password when logging in; if it contains a character that does not belong to the set { ./0-9A-Za-z }, the corresponding user cannot log in. The "last modified time" indicates the number of days from the moment when the user last modified the password. The starting point of time may be different for different systems. For example, in SCO Linux, the starting point for this time is January 1, 1970. "Minimum time interval" refers to the minimum number of days between two password changes. "Maximum time interval" refers to the maximum number of days a password remains valid. The "Warning Time" field indicates the number of days between when the system warns the user and when the user's password is officially invalidated. "Inactive Time" indicates the maximum number of days that the user has not logged in but the account remains valid. The "expiration time" field gives an absolute number of days. If this field is used, the lifetime of the corresponding account is given. After the expiration, the account is no longer a valid account and can no longer be used to log in. The following is an example of /etc/shadow: 3. All information of the user group is stored in the /etc/group file. Grouping users is a means of managing and controlling access to users in a Linux system. Each user belongs to a user group; there can be multiple users in a group, and one user can belong to different groups. When a user is a member of multiple groups at the same time, the main group to which the user belongs is recorded in the /etc/passwd file, which is the default group to which the login belongs, and the other groups are called additional groups. When a user wants to access a file belonging to an attached group, he must first use the newgrp command to make himself a member of the group to be accessed. All information about the user group is stored in the /etc/group file. The format of this file is also similar to the /etc/passwd file, separated by a colon (:) for several fields, these fields are: The "group name" is the name of the user group and consists of letters or numbers. As with the login name in /etc/passwd, the group name should not be duplicated. The "Password" field stores the encrypted password of the user group. Generally, the user group of the Linux system does not have a password, that is, this field is generally empty or *. The "group identification number" is similar to the user identification number and is also an integer used by the system to identify the group. The "in-group user list" is a list of all users belonging to this group /b], separated by commas (,). This user group may be the user's primary group or an additional group. An example of the /etc/group file is as follows: User management command Add user Create or add a new user using the useradd command, the command usage is: There are many option options for this command. The main ones are: -c Notes User sets the comment description text for the account -d home directory Specifies the home directory to replace the default / home/username -m Creates a home directory if it does not exist. -r combined with -m to create a home directory for system accounts -M does not create a home directory -e date Specifies the date the account expires. Date format is MM/DD/YY -f days The account is permanently suspended after a few days of expiration. If specified as -, it will be immediately suspended. If it is - 1, this function will be disabled. -g user group Specifies which user group to join the user to, the user group must exist The -G user group list specifies the list of user groups that the user has joined at the same time. Each group is separated by a tease. -n does not create a private user group for the user -s shell Specifies the shell to use when logging in. The default is /bin/bash -r Create a system account with a user ID less than 500. By default, the corresponding home directory is not created. -u user ID manually specifies the new user's ID value, which must be unique and greater than 499 -p password Specifies the login password for the new user. The password here is the password value obtained after the login password is encrypted by MD5, and the actual password is not true. Therefore, in practical applications, this parameter option is used less frequently, and the passwd command is usually used alone to set the login password for the user. Example: To create a user named nisj and be a member of the babyfish user group, the action command is: When adding a user, if the user group is not specified with the -g parameter, the system automatically creates a private user group with the same name as the user account by default. If you do not need to create this private user group, you can use the -n parameter. For example, add an account named nsj820, but do not specify a user group. The result of the operation is: When creating a user account, the system automatically creates the home directory corresponding to the user. The directory is placed in the /home directory by default. To change the location, you can use the -d parameter to specify it. For the shell used when the user logs in, the default is /bin. /bash, to change, is specified with the -s parameter. For example, to create an account called vodup with the home directory in the /var directory and the login shell as /sbin/nologin, the operation command is: 2. Set account properties For users who have already created, you can use the usermod command to modify and set various properties of the account, including login name, home directory, user group, login shell, etc. The usage of this command is: Part of the option option: (1) Change the user account name Implemented with the -l parameter, the command usage is: For example, to rename the user nsj820 to nsj0820, the operation command is: As you can see from the output, the username has been changed to nsj0820. The home directory is still the original /home/nsj820. If you change to /home/nsj0820, you can do so by executing the following command. (2) Lock account To temporarily disable user login, the user account can be locked. Locking an account can be done with the -L parameter, the command usage is: Linux locks the user by adding "!" in front of the password field of the password file shadow to identify that the user is locked. But through the root user, then su to the locked user, you can go in. (3) Unlock the account To unlock an account, you can do so using the usermod command with the -U parameter. 3. Delete account To delete an account, you can use the userdel command to achieve: -r is optional. If you bring this parameter, delete the account and delete the home directory corresponding to the account. To set the time when all user account passwords expire, you can do so by modifying the value of the PASS_MAX_DAYS configuration item in the /etc/login.defs configuration file. The default value is 99999, which means that the user account password never expires. The PASS_MIN_LEN configuration item is used to specify the minimum length of the account password. The default is 5 characters. 4. Set the user login password Set using the passwd command, the command usage is: If the account name is specified, the login password of the specified account is set, and the original password is automatically overwritten. Only the root user has the right to set the password for the specified account. The general user can only set or modify the password of his account (without parameters). For example, to set the login password for the nisj account, the action command is: Once the account login password is set, the account can be logged into the system. 5. Lock/unlock account password and query password status, delete account password In linux, in addition to the user account can be locked, the account password can also be locked, and if either party is locked, it will not be able to log in to the system. Only the root user has the right to execute the command. Locking the account password uses the passwd command with the -l option. The usage is: To find out if the password of the current account is locked, you can use the passwd command with the -S parameter. The usage is: E.g To delete the password for the account, use the passwd command with the -d parameter. This command is also only available to the root user. Its usage is: Once the account password is deleted, you will not be able to log in to the system unless you reset the password. 6. Create a user group Users and user groups belong to a many-to-many relationship. One user can belong to multiple user groups at the same time. One user group can contain multiple different users. Create a user group using the groupadd command, the command usage is: If the command has the -r parameter, a system user group is created. The GID value of this type of user group is less than 500. If there is no -r parameter, a normal user group is created with a GID value greater than or equal to 500. 7. Modify user group properties After the user group is created, the related attributes of the user group can be modified as needed. The modification of the user group attribute is mainly to modify the name of the user group and the GID value of the user group. (1) Change the name of the user group To rename a user group, use the groupmod command with the -n parameter to achieve: Renaming a user group does not change the value of its GID For example, to rename the student user group to the teacher user group, the operation command is: (2) Reset the GID of the user group The GID value of the user group can be modified again, but it cannot be duplicated with the GID value of the existing user group. Modifying the GID does not change the name of the username. To modify the GID of a user group, use the groupmod command with the -g parameter, which is used as: For example, to change the GID of the teacher group to 506, the action command is: 8. Delete user groups Deleting a user group is done using the groupdel command. Its usage is: When deleting a user group, the deleted user group cannot be a private user group of an account. Otherwise, it cannot be deleted. To delete, you should delete the account that references the private user group before deleting the user group. 9. Add users to the specified group / Remove users from the specified group You can add a user to a specified group to make it a member of that group. Its implementation command is: To remove a user from a user group, the implementation command is: E.g: 10. Set up user group administrators Adding a user to a group and removing a user from the group, in addition to the root user can perform the operation, the user group administrator can also perform the operation. To assign a user as an administrator for a user group, use the following command to do so; The user administrator can only perform user management on the authorized user group (adding users to or removing users from the group), and has no right to manage other user groups. 11. Other related users In addition, linux provides commands such as id, whoami, and groups to view the status of users and groups. The id command is used to display the current user's uid, gid, and the list of user groups to which it belongs; whoami is used to query the current user's name; and group is used to view the user group to which the specified user belongs. At the same time, we can use the graphical interface to manage users and user groups. System---> Administration---> Users and groups can open the corresponding configuration interface. Attached: Add a user to a user group and never use it directly: Doing so will cause you to leave other user groups and only be a member of this user group, groupA. You should use the -a option: -a stands for append, which means adding yourself to the user group groupA without having to leave other user groups.
ZGAR LEA BOX Vape
ZGAR electronic cigarette uses high-tech R&D, food grade disposable pod device and high-quality raw material. All package designs are Original IP. Our designer team is from Hong Kong. We have very high requirements for product quality, flavors taste and packaging design. The E-liquid is imported, materials are food grade, and assembly plant is medical-grade dust-free workshops.
Our products include disposable e-cigarettes, rechargeable e-cigarettes, rechargreable disposable vape pen, and various of flavors of cigarette cartridges. From 600puffs to 5000puffs, ZGAR bar Disposable offer high-tech R&D, E-cigarette improves battery capacity, We offer various of flavors and support customization. And printing designs can be customized. We have our own professional team and competitive quotations for any OEM or ODM works.
We supply OEM rechargeable disposable vape pen,OEM disposable electronic cigarette,ODM disposable vape pen,ODM disposable electronic cigarette,OEM/ODM vape pen e-cigarette,OEM/ODM atomizer device.
Disposable E-cigarette, ODM disposable electronic cigarette, vape pen atomizer , Device E-cig, OEM disposable electronic cigarette ZGAR INTERNATIONAL(HK)CO., LIMITED , https://www.zgarette.com