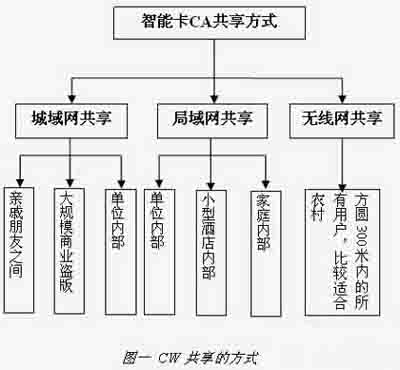
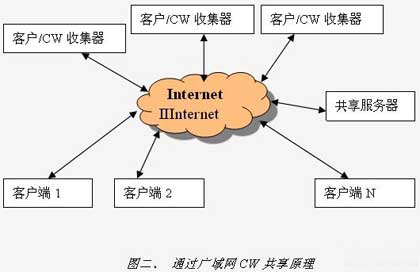
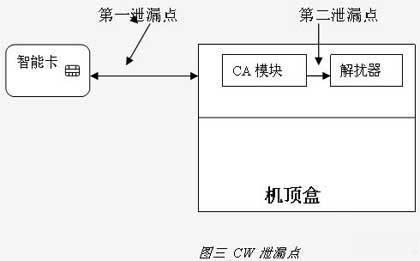
First, the question is raised This article refers to the address: http:// At present, digital TV has formed several large standard systems, such as DVB in Europe, ATSC in the United States, ISDB in Japan, etc., regardless of the transmission method, the way of obtaining the SI data containing the encrypted information in the terminal is similar, among which DVB in Europe Standards are currently the most widely used in the domestic cable TV market and have become the standard in practice and will remain unchanged for the long-term foreseeable future. In the market of satellite encrypted programs transmitted based on the DVB standard, there has been a phenomenon in which the control information of the decrypted information CW (Control Word) is transmitted through the Internet and illegally pirated, which is commonly referred to as CW network sharing. With the rapid spread of the network, this sharing is becoming more and more common and the cost is getting lower and lower. There are usually several ways to share: 1. Share over the wide area network in the area covered by the encrypted television signal. 2. By sharing in a small area on the local area network, such as a family, hotel and hotel. 3. Use a low-cost wireless connection such as ZigBee to share in a small area, such as the home. 4. Use the 232 serial port to share one child machine. The above sharing methods were first popular in the encryption of digital satellite programs in Europe and the United States, and have now spread to the whole world. Several satellite TV encrypted programs over China have been shared. The reason why CW sharing of satellite encrypted programs is more common is because satellite TV programs have higher fees, but with the increase in the value of cable digital encrypted TV programs, pirates are also becoming attractive because satellite CW sharing technology is mature. The technical threshold for CW sharing is very low. Anyone who has developed a set-top box can do the job. From satellite sharing to wired sharing, only the tuner can be replaced, so the CW sharing in the cable TV field is beginning to appear. The trend of spread. Second, the basic principle of CW network sharing The first step in CW's network sharing is to try to get CW. There are many ways to get CW: use the set-top box with genuine smart card to get the required CW, or send the ECM directly to the card reader through the computer to get CW, for example One such thing is the Phoenix Reader. The second step in CW's network sharing is to try to spread the CW out. As mentioned above, it can be through the WAN, through the LAN or wireless network, or by using a simpler RS232 serial port. This way can be used by different illegal end users to view different channels. The various sharing methods are as follows: The shared CW collector can be a card reader connected to the server, or a common network-enabled set-top box inserted into the smart card. The client inserted into the genuine smart card can also be used as a CW collector, and the shared server can be set differently, or not. The same city, not even in the same country, has brought great difficulties to the investigation. If the P2P protocol is embedded in the set-top box, even the server does not need it. As the set-top box runs faster, the set-top box is bi-directional. If the software is upgraded, the set-top box itself can become a shared server, and CW sharing will be easy to flood. Third, the reasons for CW sharing The main reason why CW sharing can occur is that the broadcast DVB architecture design itself is derived from the unilateral over-reliance of smart cards on the confidentiality of each CA company. As far as the DVB architecture design itself is broadcast, each set-top box has the same lock (descrambler). Different program packages have different keys (CW). The role of CAS is to be responsible for encrypting. The back key (ECM) is safely sent to the smart card inserted in the set-top box to re-decrypt to obtain CW. CW is the object that all CAS tries to encrypt and protect. In the DVB secret architecture, different CASs only have different encryption and decryption algorithms. However, the CW obtained after decryption is the same. If it is easy to get CW, all the efforts of CAS will be abandoned. The so-called first-level encryption secondary encryption, and all efforts to increase the key length will be ineffective. Since CW is common to all set-top boxes and there is no way to dye it and increase the difference, it is impossible to track the source of CW, and operators and CA suppliers can only passively protect. Today's CA providers generally treat library files containing communication with smart cards as highly confidential and authorize them to be embedded in the set-top box manufacturers. The more authorized manufacturers, the more people know the secret, and the leakage point of CW Fully exposed to participating in this embedding. But this is difficult, because there is no clear legal definition of this kind of sharing, and the amount involved in the illegal act is not large, and because the server is easily and widely dispersed, even a set-top box itself can be used. A server, if the operator corresponds to a group of shared servers, it will be a very helpless thing, if it is to face a family or internal sharing, it will be even more helpless. Furthermore, if the shared technology provider uses P2P technology in the computer network for sharing, it is even more difficult to track. For the CAS with low technical level, after the failure of the technical means, the CA supplier can only mobilize the operators to rely on this way to remedy. (5), do not need a smart card, directly embed the decryption algorithm into the set-top box Since there are many ways to get CW, if all decryption actions are inside a closed set-top box, CW will not be visible. This CA method has been popular in North America many years ago and is a very advanced digital TV encryption system, and there is no record of being shared and cracked. It is the future development trend of CA technology, which can eradicate the aftermath of sharing CW. This may be the ultimate solution to the problem of digital TV security. Because of the complexity of the technology involved in this solution, CA has few such comprehensive design capabilities. In front of CA engineers, designing a CW-shared set-top box is a breeze for these engineers. Network sharing is also a matter of recent years. When the DVB standard was formulated more than ten years ago, I believe that no one would think that network sharing would become the nemesis of smart card CA. This kind of sharing is common even in Europe and the United States where legal protection is very strict. Operators are powerless, and its harm to operators in China in the future can be imagined. There are two places to get CW: one is the machine card communication process; the other is to embed the backdoor program in the set-top box, intercept it before the CA library sets the CW to the descrambler, or simply read it from the register that stores the CW, and then Spread through the serial port or the network; other methods are very difficult. Fourth, the solution to the problem and the corresponding problem From the previous analysis, it can be seen that the problem of solving CW sharing should be how to make the sharer unable to obtain CW, or increase the difficulty of obtaining CW, and there is no other good way. Here are some corresponding solutions to get attention and find the final solution. (1) CW encrypted communication between set-top box and smart card This may be the only solution for the CA system of the smart card system. For the method of stealing the plaintext CW from the set-top box and the smart card communication process, the communication between the set-top box and the smart card is encrypted, and the plaintext transmission is not used. However, this kind of preventive measures can only solve part of the problem, and can only prevent hackers with low levels. The encryption algorithm and key of the encrypted communication method are easily obtained from the library files provided by the CA vendor, and can also be disassembled. The way to get it from the flash memory, it only takes more time, and the level of hacking needs to be higher. If a large number of smart cards have been issued, and a large number of set-top boxes, if the variety of set-top boxes is large, the set-top boxes and smart cards are difficult to upgrade, and the CW is transparently transmitted. To maintain the versatility and continuity of the CA, there is no improvement. Operators who choose this low-level CA can only rely on network sharing. (2), set a security chip between the set-top box and the smart card This method is also called a secure set-top box. In fact, a secure path is set between the smart card and the set-top box descrambling circuit. The decryption algorithm for storing the key and transmitting the CW inside the security chip is also within the smart card. Store the corresponding key and algorithm. The difference from the above CW encrypted communication is that the encryption algorithm is placed in the security chip. This kind of preventive measure should be said to be a better way at present, but it can only be suitable for the newly introduced CA. The old version of CA can't do anything about it. Since a security chip is added and can only be used for the same CA system, it cannot be mass-produced, and the cost of the operator CA system is also increased. This method actually converts the encrypted transmission of CW from software to hardware, and CW still needs to be obtained from an external smart card. If the security chip is cracked, there is also a risk of CW sharing, which is not the final solution. (3) Take countermeasures from the front end The countermeasures are mainly the technical means adopted by the operators and CA manufacturers according to the situation. There are three measures that can be taken now: 1. Adjust the transmission frequency of the ECM. By increasing the transmission frequency of the ECM, a large number of users sharing the CW through the network, due to the slow transmission speed, receiving the CW is not timely, resulting in a black screen. However, these measures often make the normal and legitimate set-top box users unable to use normally, and can only work within a certain range. 2. Smart card positioning and locking. It should be a very troublesome thing. Faced with dozens of millions of users, finding the smart card that is being used illegally can not affect the use of normal users, just like finding a needle in a haystack. 3. Send an ununderstood command so that the card reader on the shared server does not work properly. The effect of this kind of measure is limited. People who develop smart card CA will not think of leaving a command to control sharing in the future. If he thinks, he may not develop smart card CA. (4), sharing tracking measures, taking legal sanctions If sharing occurs, check the person responsible for setting up the shared server V. Outlook Based on the DVB framework, the smart card CA technology has a history of more than ten years. The design of the smart card conditional access system is no longer mysterious. Many companies have the design capability of this smart card CA technology; lack of innovation is the result of traditional smart card CA security. The root cause of hidden dangers. CW sharing is an inevitable defect of smart card CA technology. Bidirectionalization can not solve this problem. On the contrary, it will cause sharing flood. By upgrading the two-way set-top box, you can directly convert a large number of two-way set-top boxes into shared set-top boxes. Ordinary one-way set-top boxes can be turned into two-way set-top boxes by adding a small module, and this kind of hidden danger exists. If smart card-based security measures are taken, hackers can easily obtain CW even if the CW is opaque between the set-top box and the smart card, and so far there is no solution to prevent hackers from obtaining CW. In a sense, all CASs that use smart cards currently have this problem, which is a common challenge for all smart card CAS vendors. Solving the problem of CW sharing requires not only the efforts of the CAS provider, but also the support of the set-top box hardware and software environment. If you want to completely solve the security problem of this DVB encryption and decryption system, you must get rid of the reliance on the smart card CA, throw away the smart card, and find other solutions.
This Fiber Optic Cable Protection Box is an Indoor Fiber Optic Cable Protection Box (also known as Heat Shrinkable Tube Box or FTTH Drop Splice Closure). It is a case to put in a butterfly cable with a thermal protection tube after hot melting, so that the splice spot can get a better protection. Relative to the cold welding, the hot one can improve the optical performance of connector, make the effective connection rate increased to one hundred percent, prolong the service life of the product and lower maintenance costs.
The fiber optic Cable Protection Box produced is made of advanced production technology. The surface gloss of the box is uniform and beautiful, the material is strong and durable, the interior structure is reasonable, and it can fully meet the construction requirements of 1 in 1 out, 1 in 2 out / 4 out, 2 into 2 out / 4 out. Adopting reinforced plastics, high strength, corrosion resistance, mature structure, reliable sealing and convenient construction.
Cable Protection Box,Fiber Drop Cable Protection Box,Fiber Optic Cable Protection Box,Drop Cable Protection Box Chengdu Xinruixin Optical Communication Technology Co.,Ltd , https://www.xrxoptic.com